Surface Single Sign On
Introduction
Surface provides the ability to use Single Sign On with the enosix SAP Framework through enosix Link. When configured, a user will login to their Salesforce organization using their organizational identity provider and interact with their SAP data through Salesforce. This page will illustrate this configuration using Microsoft Azure Active Directory.
Prerequisites:
The XSUAA provider must be configured. In this example we will need Azure Active Directory configured as an identity provider in XSUAA.
Overview
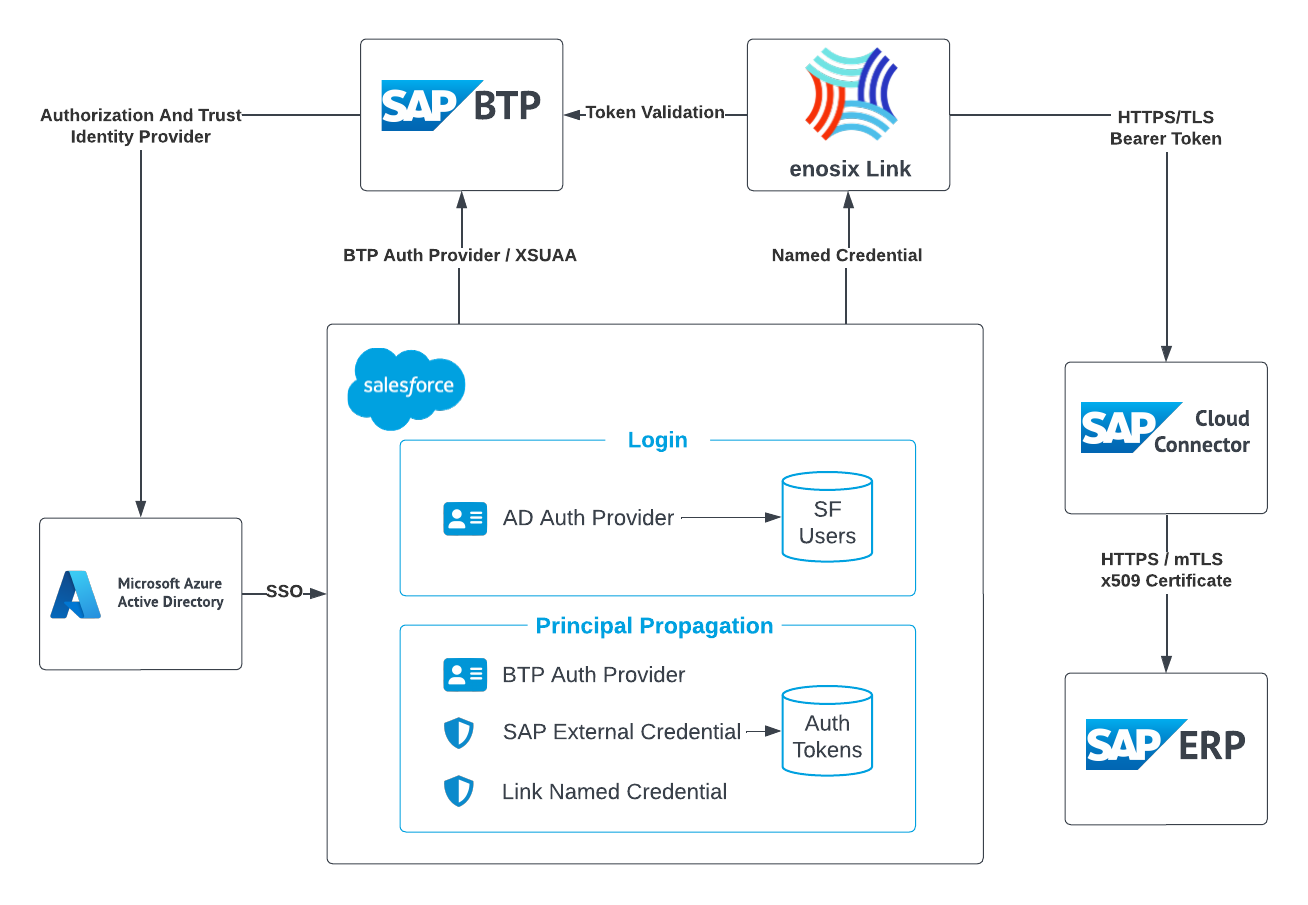
- When configured according to the diagram above, a user will use Single Sign-on to login to their Salesforce organization using the Microsoft Azure Active Directory identity provider. This is configured using an Open ID Auth Provider (AD Auth Provider)
- Once logged in, a user is able to access SAP data by authenticating to SAP BTP (BTP Auth Provider), which has been configured to use the same Active Directory Identity Provider. Salesforce will initiate an auth flow that will create a token used for authenticating and validating the Active Directory user to enosix Link and SAP Cloud Connector.
- SAP Cloud connector will perform the auth token to certificate mapping for authentication to SAP ERP (ECC & S4 Hana). Generally, this mapping is between a user's email address obtained from Azure Active Directory to a user's SAP ERP User record. The Mapping of emails to SAP users is maintained in the SAP system.
- To ensure a user's SAP auth token is created during login, a Visual Force Page can be used during the organization's Login process to create the Auth tokens for accessing SAP systems. This will ensure when a user accesses a page with an enosix data virtualization component on it, they will already be authenticated to the SAP system.
- The token credentials for accessing the SAP system will be stored securely in Salesforce (SAP External Credential), and can be shared between many named credentials for various SAP ERP systems.
Configuring enosix Link for SSO
Single sign-on requires enosix Link to be configured for Principal Propagation.
Configuring Auth Providers in Salesforce
- Configure the Login Auth. Provider The first authorization provider is needed in order for an organization's users to login to their Salesforce org using Azure Active Directory. This can be configured by following Example provided by Salesforce
If you already have SSO configured into Salesforce, this step is not required.
- The first step under the Set Up an Azure AD Application step in the Salesforce documents has a broken link(
https://manage.windowsazure.com). Instead, use https://portal.azure.com. - The Keys referenced in the Salesforce documentation refer to Client secrets and can be found under Certificates & Secrets.
- The instructions for Create an Azure Auth. Provider in Salesforce no longer provide valid Azure AD endpoints. You can find your endpoints for your application by following Microsofts Documentation around Endpoints.
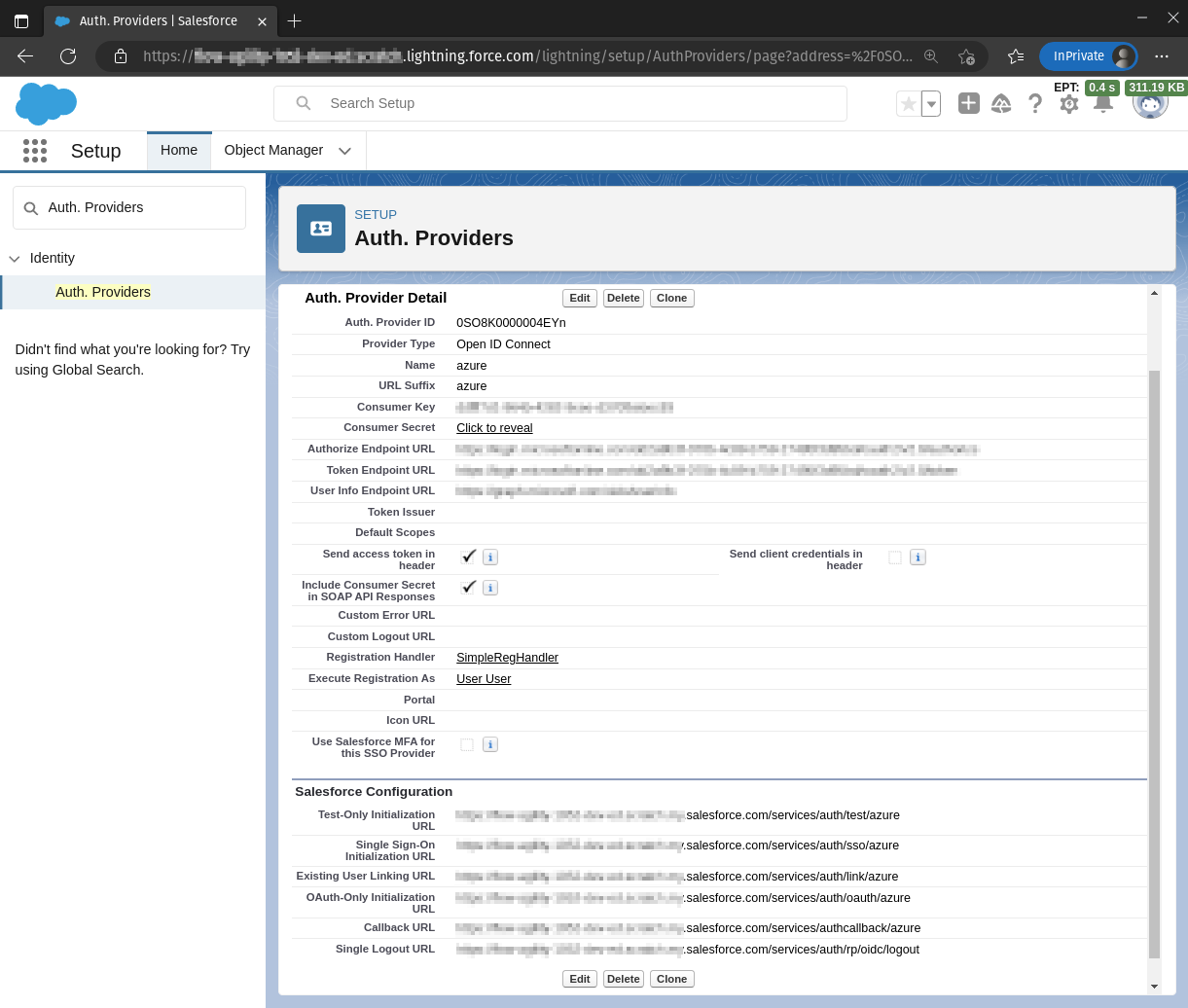
A completed Azure Auth. Provider (named azure):
- Configure the Principal Propagation Auth. Provider
The second authorization provider is needed to provide an auth token tied to the SAP External Credential. This Auth. Provider can be configured by following these steps:
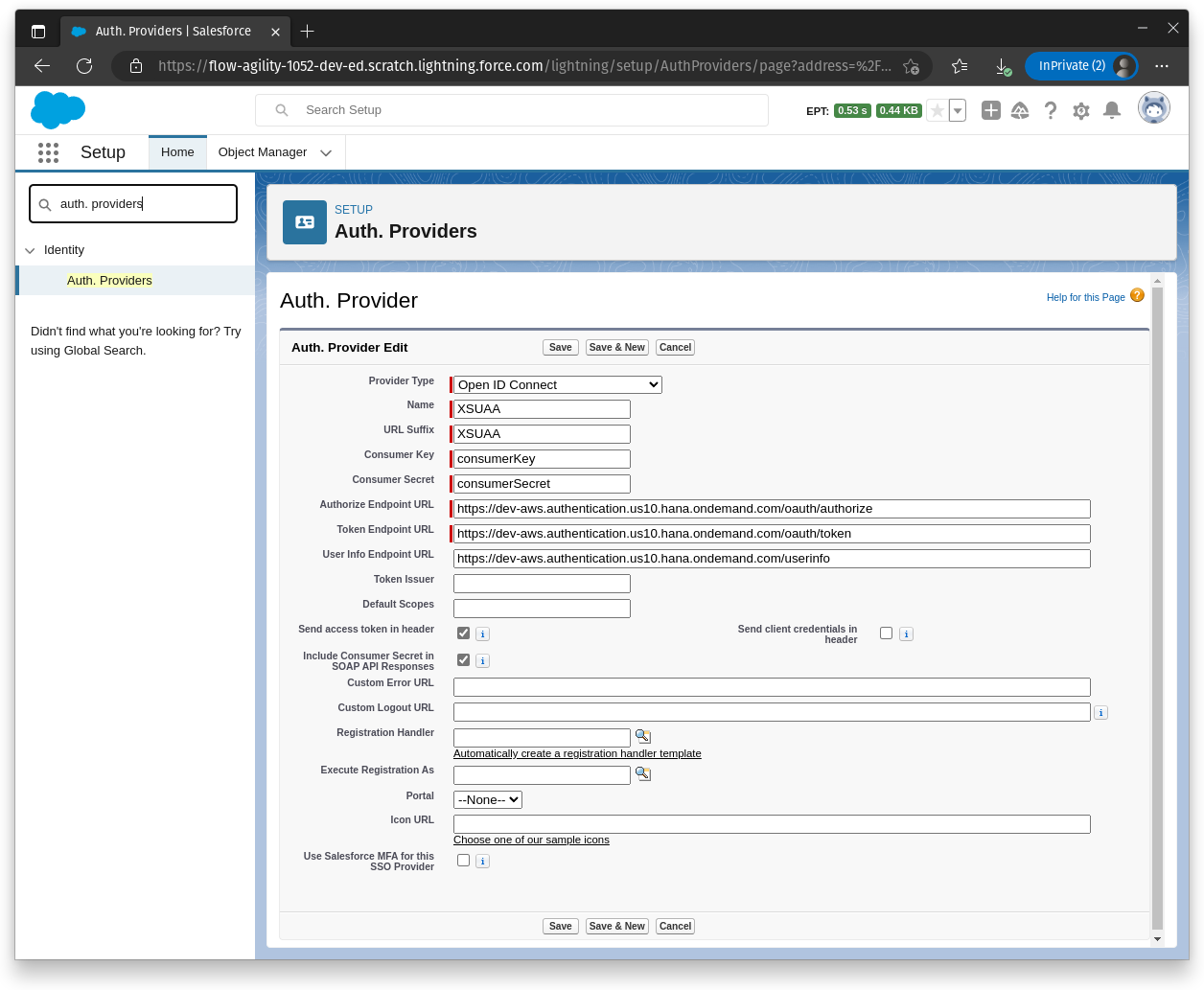
- From Setup, enter Auth. Providers in the Quick Find box, and select Auth. Providers | New.
- For the provider type, select Open ID Connect.
- Enter a name for your Auth. Provider, such as XSUAA. Salesforce uses this name as the URL suffix in the callback URL, which is how the application responds to the Salesforce authentication request. For example, if the name and suffix combination is XSUAA, your SSO URL is similar to https://mydomain_login_url or site_url/services/auth/sso/XSUAA.
- For Consumer Key, paste the
clientid. - For Consumer Secret, paste the
clientsecret. - Enter the XSUAA endpoints by opening
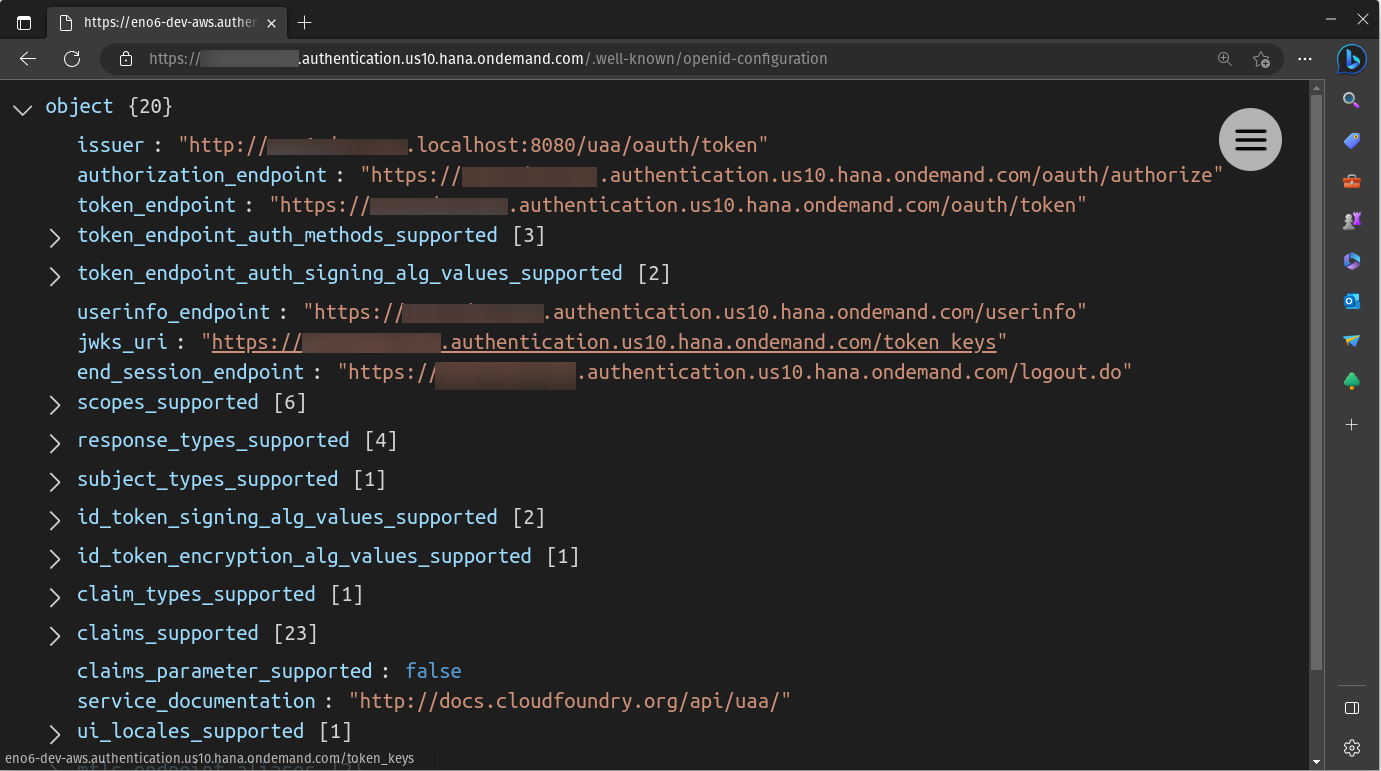
https://<url>/.well-known/openid-configuration- Authorize Endpoint URL=
https://<url>/oauth/authorize - Token Endpoint URL=
https://<url>/oauth/token - User Info Endpoint URL=
https://<url>/userinfo
noteThe Authorize Endpoint URL, Token Endpoint URL, and User Info Endpoint can be found by accessing the URL from the Authorization and Trust Management Service credentials screen with the path
/.well-known/openid-configuration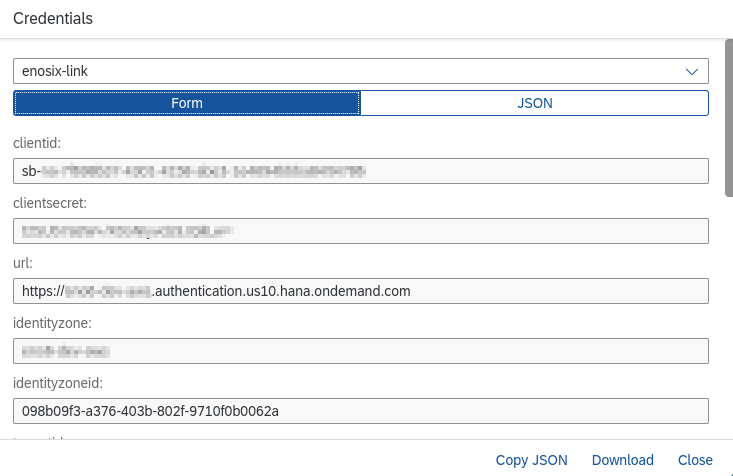
- Authorize Endpoint URL=
- Save the settings.
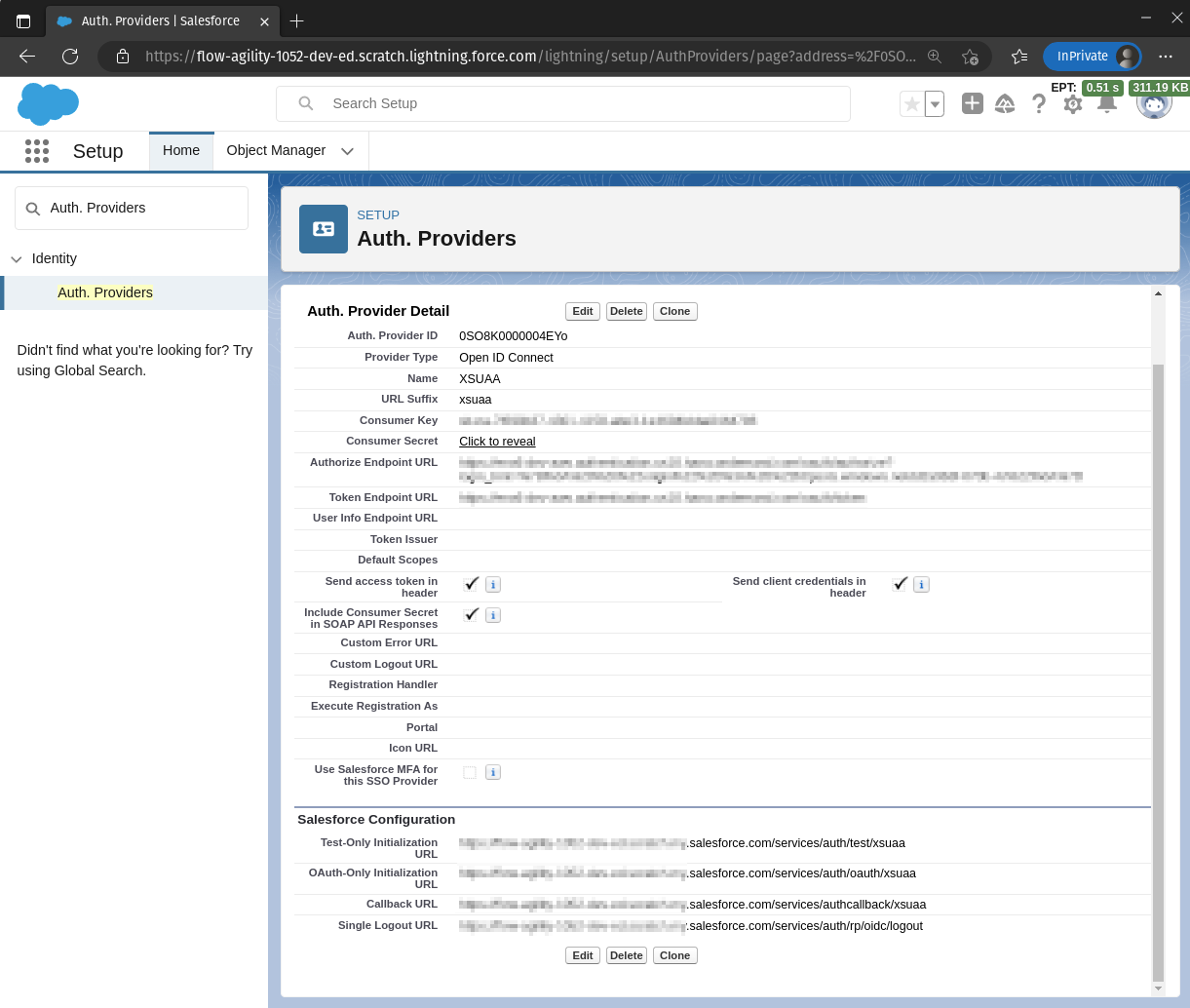
A completed Principal Propagation Auth. Provider (named XSUAA):
Configure the External Credential for SAP
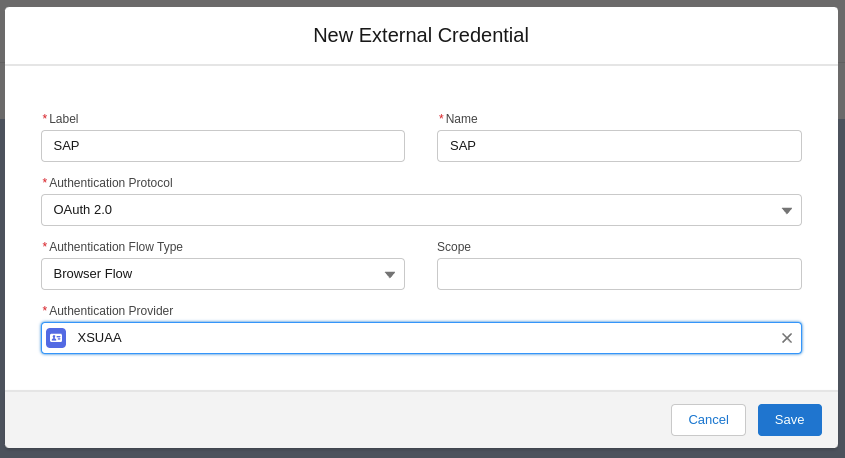
An external credential using OAuth 2.0 Browser Flow needs to be configured for the Principal Propagation Auth. Provider. This can be configured by following the Example provided by Salesforce.
A completed External Credential named SAP:
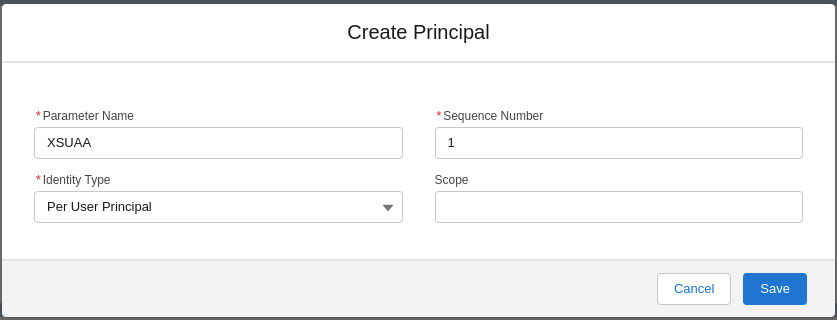
The External Credential also needs to have a Principal configured with a Per User Principal identity type.
A completed Per-User Principal config named XSUAA:
Configuring a Named Credential for the enosix Framework
A named credential will need to be configured using the External Credential you just created and pointing to your enosix Link route configured for Principal Propagation.
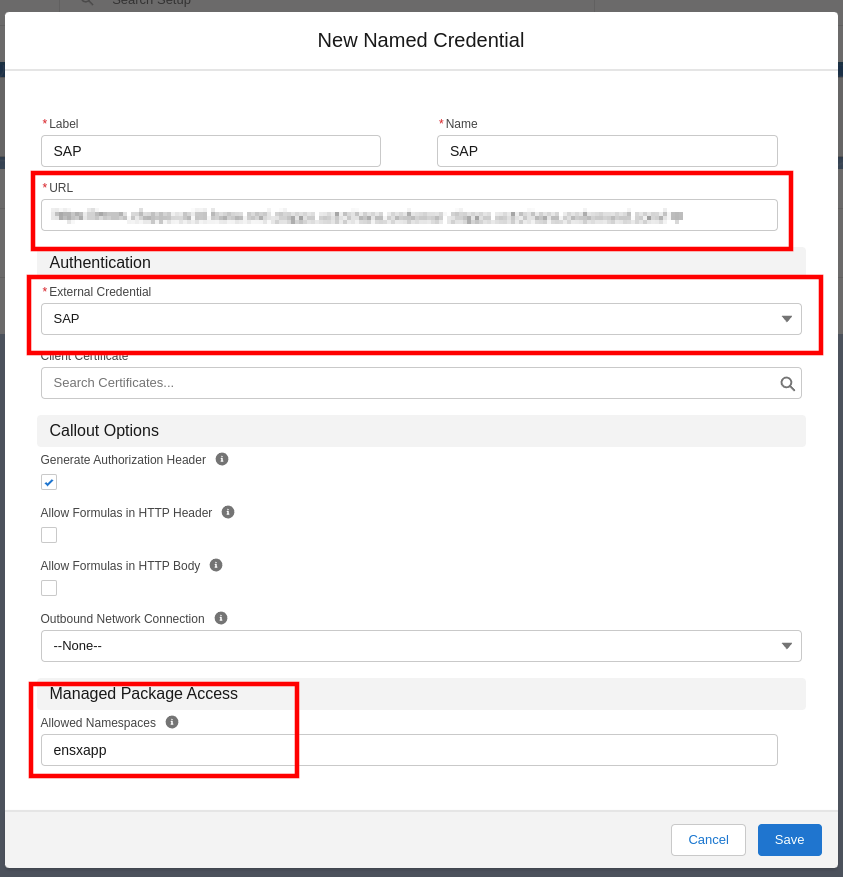
For SSO to work with enosix Salesforce Components, the ensxapp needs to be added to the Managed Package Access: Allowed Namespaces
A completed Named Credential config named SAP:
Create a permission set for External Credential Principal access
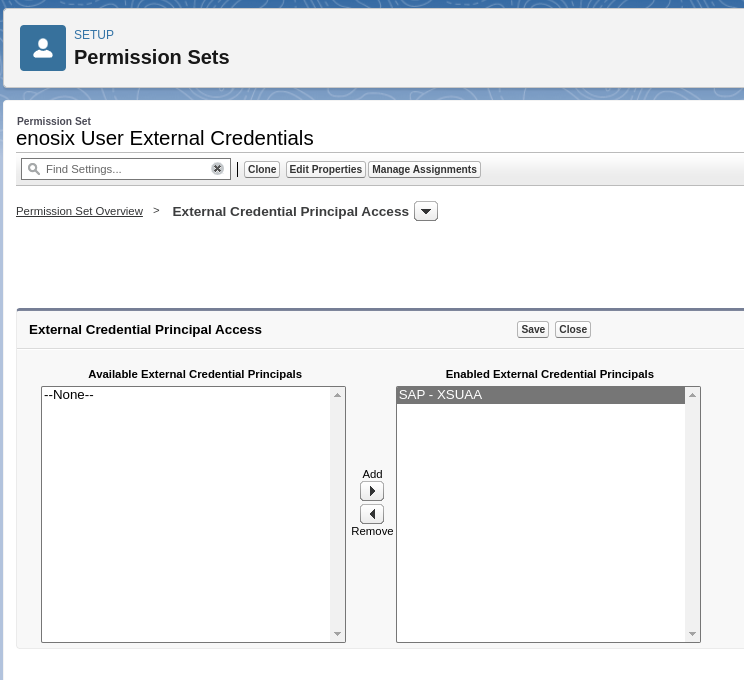
A permission set needs to be created that grants a user access to the Per-User External Credential Principal (ex, SAP - XSUAA), as well as access to the User External Credential object.
- Create a new permission set named
enosix User External Credentials - Under
Apps->External Credential Principal Access, click edit - Grant access to the Per-User External Credential Principal just created.
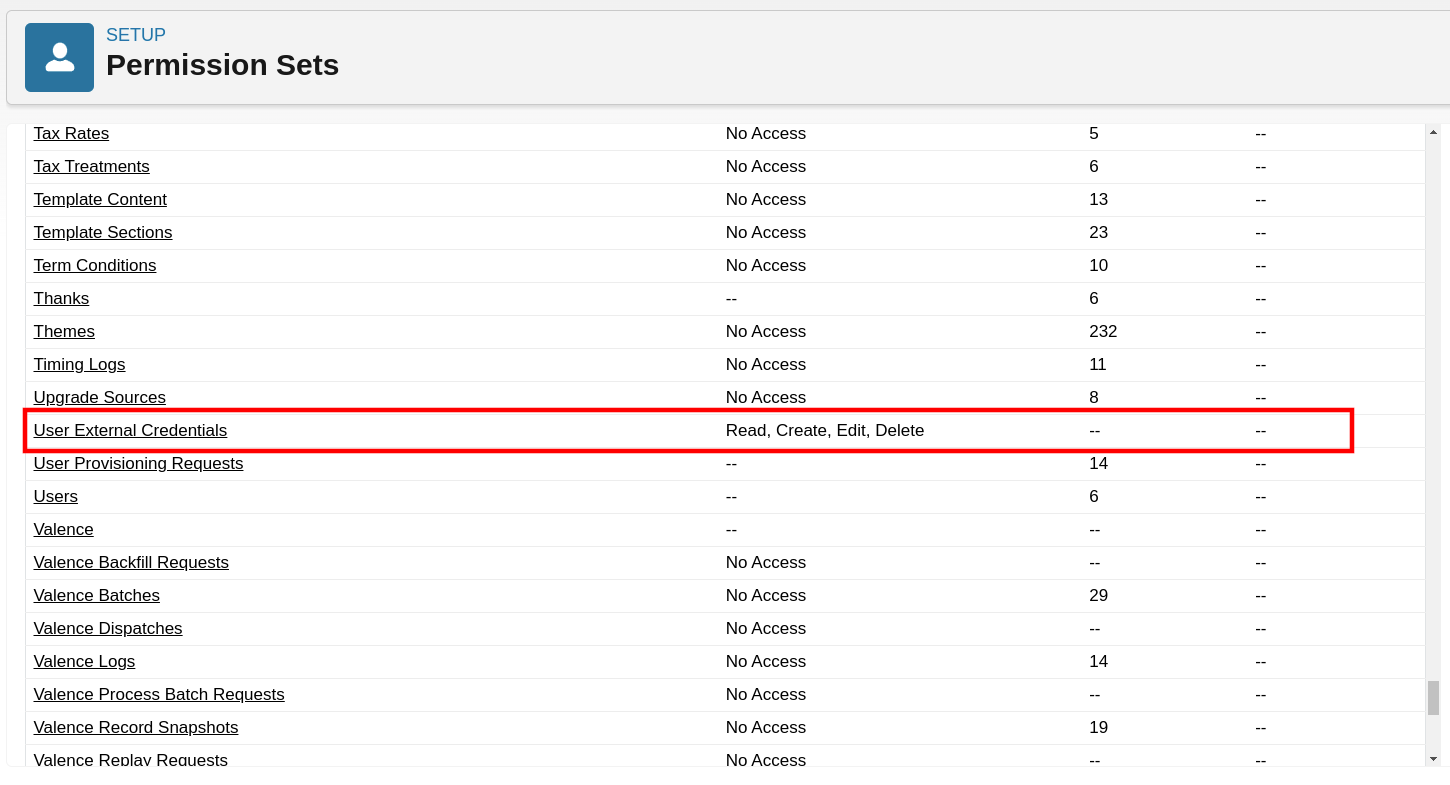
- Grant Read, Create, Edit, Delete access on the User External Credentials object.
A completed permission set named enosix User External Credentials:
Users of enosix Salesforce components will need to be granted this permission set, as well as either the enosix App Standard User or enosix App Admin permission set.
Configure enosix Framework to use the Named Credential
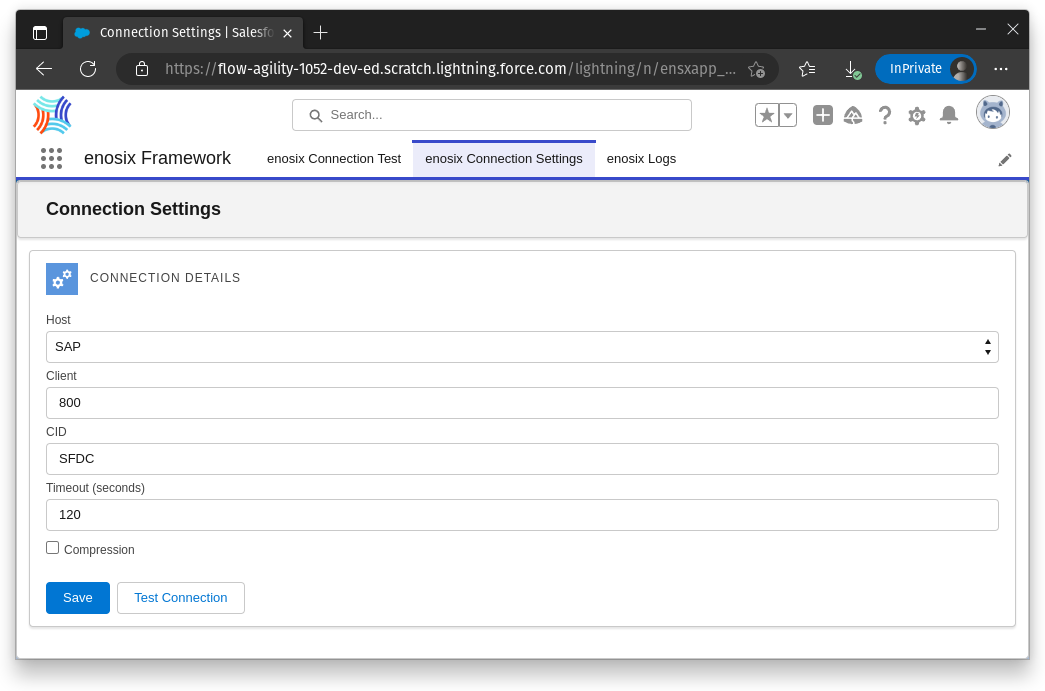
- As a user with the enosix App Admin permission set, use the Application Launcher to open the enosix Framework application.
- On the enosix Connection Settings tab, change the settings so the Host is using the named credential you've just created and Save.
Authenticate External Credential
When users login to the Salesforce organization with the Active Directory Auth. Provider, they still need to authenticate the External Credential.
-
Click on
User Profile -
Click on
Settings
-
Click on
External Credentials -
Click on
Allow Access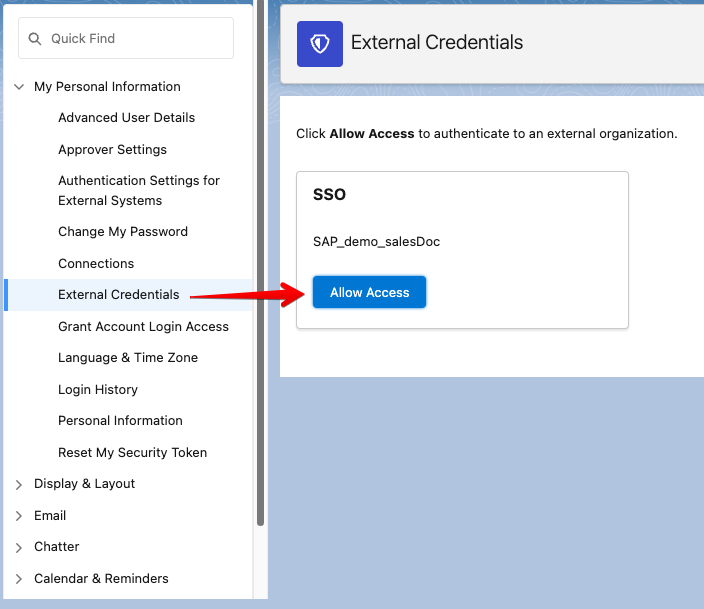
-
You should now have a green
Configuredstatus indicating you are now authenticated using your External Credential.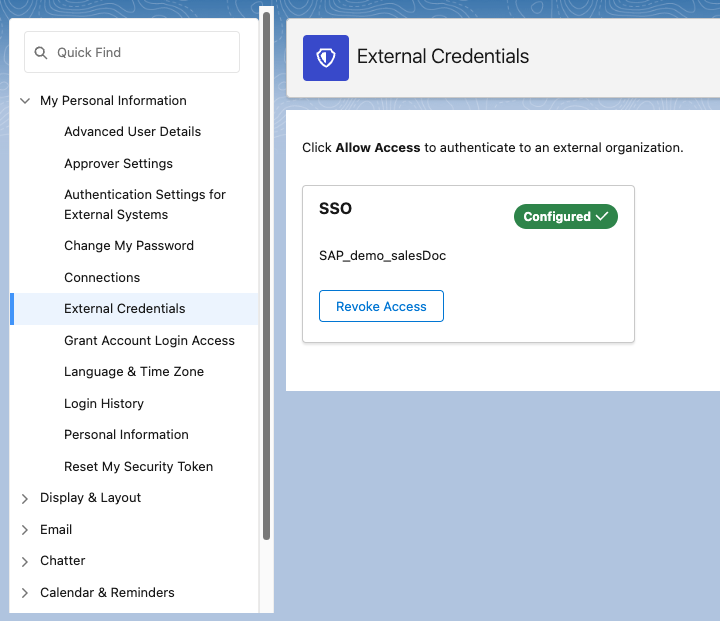
It is advised not to use a Login Flow to automate this process.